Trezor Login: A Secure Gateway to Your Crypto Wallet
The Trezor Login process is your secure entry point to managing digital assets safely using Trezor’s hardware wallets. In today’s environment of increasing cyber threats, using Trezor Login ensures that your private keys remain offline and out of reach from hackers.
Why Trezor Login Is Crucial for Crypto Security
When it comes to cryptocurrency, security is everything, and Trezor Login offers a robust line of defense by keeping your credentials and keys protected within a hardware wallet environment. With Trezor Login, you mitigate phishing risks and shield your assets from online vulnerabilities.
How Trezor Login Works with Trezor Suite
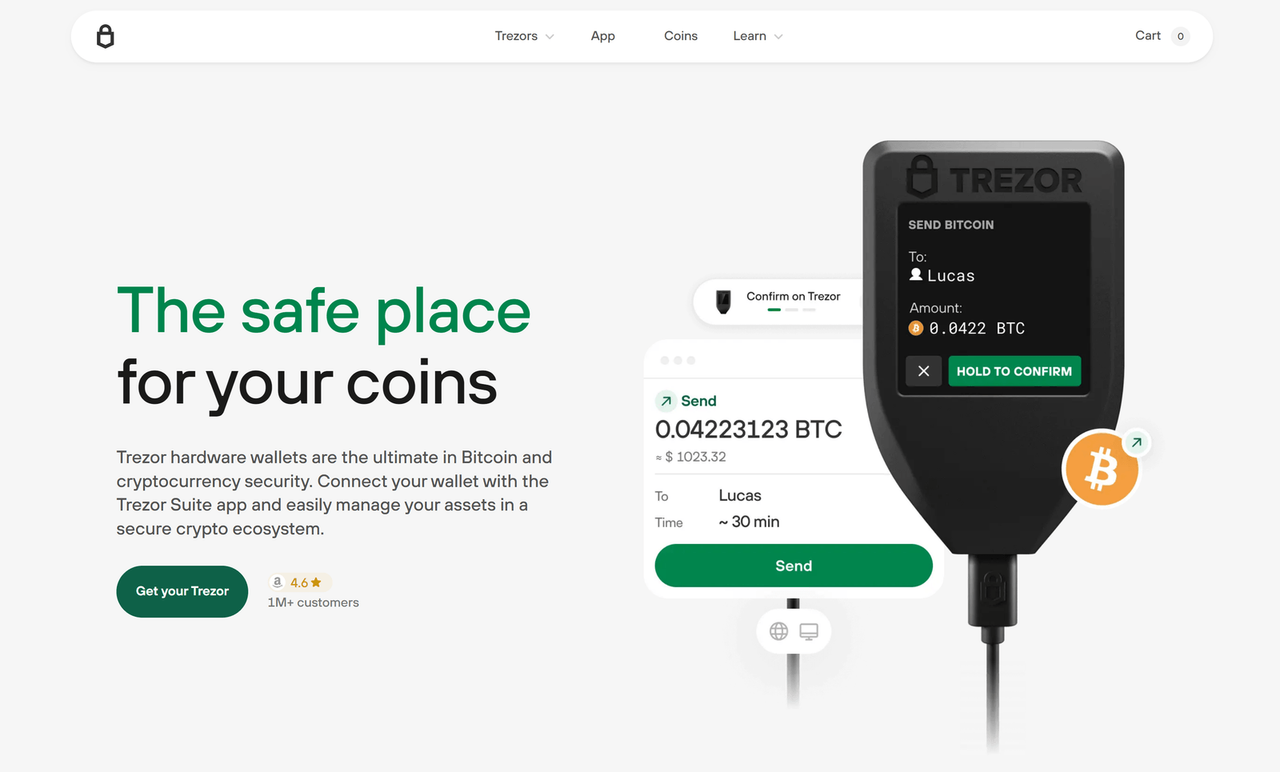
Using Trezor Login with Trezor Suite gives you access to a user-friendly dashboard for managing coins, tokens, and settings. Every time you initiate a Trezor Login, your device confirms the action, keeping your data safe and allowing only authorized access.
Trezor Login vs. Traditional Passwords
Unlike traditional online logins that rely on passwords alone, Trezor Login utilizes physical device confirmation, which makes it virtually impossible for unauthorized parties to gain access. Trezor Login eliminates the need to remember or store complex passwords.
Trezor Login for Beginners: What You Need to Know
If you're new to crypto, understanding Trezor Login is an essential first step. Trezor Login is the authentication method you use to access your wallet using a Trezor Model One or Model T, ensuring that you, and only you, can approve transactions.
Benefits of Using Trezor Login with Your Wallet
One of the biggest benefits of Trezor Login is full control over your private keys and seed phrase. Trezor Login ensures no third-party stores your data, giving you true ownership over your digital assets with peace of mind.
Step-by-Step Guide to Trezor Login
To help you get started with Trezor Login, follow these essential steps. Trezor Login doesn’t require advanced knowledge — just a few simple actions to keep your funds secure.
- Connect Your Device: Begin the Trezor Login process by plugging your Trezor into your computer via USB.
- Launch Trezor Suite: Open the Trezor Suite app to initiate Trezor Login and view your assets securely.
- Confirm on Device: During the Trezor Login, approve access requests using the buttons on your Trezor device.
- Enter Passphrase (if set): If you’ve configured a passphrase, Trezor Login will prompt you to enter it before gaining access.
- Wallet Access Granted: Once the Trezor Login completes, you can view balances, send or receive crypto, and manage settings safely.
Trezor Login for dApps and Web3 Platforms
You can also use Trezor Login to authenticate with decentralized applications (dApps) like Uniswap, Aave, or Metamask-compatible platforms. With Trezor Login, your hardware wallet becomes your Web3 passport — secure and always under your control.
Trezor Login Troubleshooting Tips
If you ever encounter issues during Trezor Login, ensure your firmware is up to date, cables are functional, and your browser supports Trezor Bridge. These small checks can restore a smooth Trezor Login experience.
Trezor Login and Advanced Security Features
Security doesn’t stop with just Trezor Login. You can enable hidden wallets, create multiple accounts, and use custom passphrases — all enhanced by the protection Trezor Login provides at its core.
Trezor Login: Compatible Coins and Networks
Trezor Login supports a wide range of cryptocurrencies including Bitcoin, Ethereum, Litecoin, Cardano, and ERC-20 tokens. With Trezor Login, you can manage multiple coins across various chains with a single secure interface.
Trezor Login: Cloud-Free, Hacker-Proof Access
Unlike browser-based wallets, Trezor Login never exposes your credentials to the cloud. Trezor Login is inherently more secure because it requires physical confirmation and offline key management.
Trezor Login in the Era of AI and Cybersecurity Threats
As AI tools become more advanced, phishing attacks and identity theft also evolve. Trezor Login stands as a modern defense mechanism, combining hardware encryption and user confirmation to safeguard digital identities. Trezor Login ensures you're protected in this digital arms race.
Conclusion: Make Trezor Login a Daily Habit
Integrating Trezor Login into your crypto routine means choosing peace of mind. Whether you're a seasoned investor or a beginner, Trezor Login empowers you to take full control of your digital wealth. The more you rely on Trezor Login, the safer your assets remain from online threats and unauthorized access.
Made in Typedream